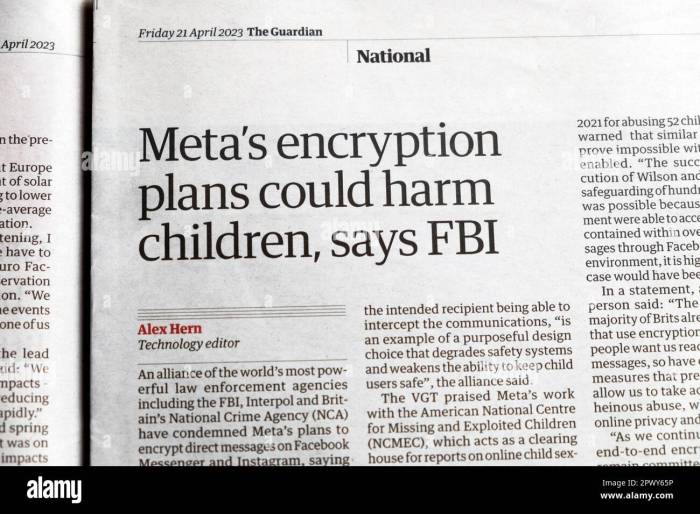
Uk targets meta encryption plans child sexual abuse concerns – UK Targets Meta Encryption Over Child Abuse Concerns: The UK government is expressing serious concerns about Meta’s encryption plans, arguing that they could hinder efforts to combat child sexual abuse material (CSAM). This clash between privacy and safety raises critical questions about the balance between protecting users’ online communication and safeguarding vulnerable individuals.
Meta, on the other hand, maintains that encryption is essential for user privacy and security, emphasizing that it enhances communication protection. The company argues that its encryption plans are designed to safeguard user data and prevent unauthorized access. The debate centers on the potential impact of encryption on law enforcement’s ability to investigate and prevent CSAM while respecting individual privacy.
UK’s Concerns Regarding Meta’s Encryption Plans
The UK government has expressed significant concerns regarding Meta’s plans to implement end-to-end encryption across its platforms, particularly in relation to the potential impact on efforts to combat child sexual abuse material (CSAM). The government argues that such encryption could create a safe haven for perpetrators, making it more difficult for law enforcement agencies to detect and investigate child abuse cases.
Concerns Regarding Child Sexual Abuse Material
The UK government’s primary concern is that end-to-end encryption could make it significantly more challenging for law enforcement agencies to access and investigate CSAM. The government argues that encryption would effectively create a “black box” for communications, making it difficult to monitor and intervene in cases where children are being abused.
“End-to-end encryption would create a barrier to law enforcement access to data that is essential for investigating and prosecuting serious crimes, including child sexual abuse.”
UK Home Secretary, Priti Patel
Investigate the pros of accepting dutch quantum spinout funding qubit testing tech in your business strategies.
Examples of Potential Hindrances
- Identifying and Removing CSAM:Law enforcement agencies often rely on metadata and content analysis to identify and remove CSAM from platforms. End-to-end encryption would prevent access to this information, making it more difficult to detect and remove abusive content.
- Investigating Child Exploitation Networks:Law enforcement agencies rely on access to communications data to investigate child exploitation networks and identify perpetrators. Encryption would hinder this process, potentially allowing perpetrators to operate with greater anonymity and impunity.
- Protecting Children:The UK government argues that end-to-end encryption could put children at greater risk of exploitation and abuse by making it more difficult to identify and stop perpetrators.
Meta’s Encryption Plans and Their Impact
Meta’s encryption plans, a key element of their strategy to enhance user privacy and security, have sparked significant debate. While Meta argues that encryption strengthens user protection, concerns have been raised about its potential to shield malicious actors and hinder law enforcement efforts in combating child sexual abuse material (CSAM).
Meta’s Encryption Plans and Their Intended Benefits
Meta’s encryption plans aim to secure user communications across its platforms, including Facebook, Instagram, and WhatsApp, by scrambling data in transit and at rest. This means that even Meta itself cannot access the content of private messages. Meta argues that encryption is essential for protecting user privacy and security in an increasingly digital world.
They highlight the benefits of encryption, such as:
- Enhanced User Privacy:Encryption ensures that only the intended recipient can access the information, preventing unauthorized access and protecting sensitive data from prying eyes.
- Increased Security:Encryption makes it much harder for malicious actors to intercept and exploit user data, reducing the risk of cyberattacks, data breaches, and identity theft.
- Trust and Confidence:Encryption fosters trust between users and platforms by demonstrating a commitment to data protection and security, encouraging users to share information more freely.
Meta’s Encryption Plans and Their Differences from Existing Practices
Meta’s encryption plans represent a significant shift from their existing practices, which allowed them to access and scan user content in certain cases. This shift reflects a growing trend towards end-to-end encryption across the tech industry, driven by concerns about user privacy and the increasing sophistication of cyber threats.
Meta’s plans are distinct from existing practices in several ways:
- End-to-End Encryption:Meta’s plans involve implementing end-to-end encryption, meaning that messages are encrypted from the sender’s device to the recipient’s device, and no third party, including Meta, can access the content.
- Expansion of Encryption Coverage:Meta plans to expand encryption coverage to include more platforms and communication channels, including private messages on Facebook, Instagram, and WhatsApp.
- Limited Access for Law Enforcement:Under Meta’s encryption plans, law enforcement agencies would have limited access to encrypted content, requiring legal warrants and specific procedures to access data.
Meta’s Argument for Enhanced Privacy and Security
Meta argues that encryption is essential for protecting user privacy and security in an increasingly digital world. They contend that encryption provides a crucial layer of protection against cyber threats, such as data breaches and identity theft, while also safeguarding users’ right to privacy.
Meta’s argument rests on the following points:
- Data Breaches and Identity Theft:Encryption makes it significantly harder for malicious actors to steal user data, reducing the risk of data breaches and identity theft.
- Cyberattacks and Malware:Encryption helps to prevent cyberattacks and the spread of malware by making it more difficult for attackers to access and exploit user data.
- Government Surveillance:Encryption provides a safeguard against government surveillance, protecting users from unauthorized access to their communications and data.
- User Trust and Engagement:Encryption fosters trust between users and platforms, encouraging users to share information more freely and engage more actively in online communities.
The Balancing Act
The debate surrounding Meta’s encryption plans highlights a fundamental tension between privacy rights and the need to combat child sexual abuse material (CSAM). This tension necessitates a careful analysis of the ethical and legal implications of balancing these competing interests.
Ethical and Legal Implications
The ethical and legal implications of balancing privacy rights with the need to combat CSAM are complex and multifaceted. On the one hand, the right to privacy is a fundamental human right enshrined in international law. It protects individuals from unwarranted intrusion into their personal lives and communications.
On the other hand, the protection of children from exploitation and abuse is a paramount moral and legal obligation. This obligation requires robust measures to prevent and combat CSAM. The challenge lies in finding a balance between these competing interests.
End-to-end encryption, while enhancing privacy, can create a “dark space” where CSAM can be shared without detection. Conversely, weakening encryption to facilitate detection raises serious concerns about privacy violations and the potential for misuse of access to private communications.
Arguments for and Against End-to-End Encryption
The debate surrounding end-to-end encryption in relation to child protection is polarized, with strong arguments on both sides.
Arguments for End-to-End Encryption
- Enhanced Privacy:End-to-end encryption protects users’ communications from unauthorized access, including government surveillance. This is essential for safeguarding sensitive information, promoting free speech, and protecting individuals from harassment and intimidation.
- Security Against Hacking and Data Breaches:End-to-end encryption makes it extremely difficult for hackers and cybercriminals to intercept and steal sensitive data. This is crucial in an era of increasing cyber threats and data breaches.
- Protection of Whistleblowers and Journalists:End-to-end encryption allows whistleblowers and journalists to communicate securely, without fear of reprisals or censorship. This is essential for holding powerful institutions accountable and protecting freedom of the press.
Arguments Against End-to-End Encryption
- Increased Difficulty in Detecting CSAM:End-to-end encryption makes it more challenging for law enforcement agencies to detect and investigate CSAM. This can hinder efforts to protect children and bring perpetrators to justice.
- Potential for Abuse by Perpetrators:End-to-end encryption could create a safe haven for CSAM perpetrators, allowing them to share and access illegal content without fear of detection. This could lead to an increase in child exploitation and abuse.
- Erosion of Trust and Transparency:Weakening encryption to facilitate surveillance could erode trust in technology companies and undermine the principles of transparency and accountability. This could have negative implications for user privacy and freedom of expression.
Potential Solutions and Compromises
Finding a balance between privacy and security requires innovative solutions and compromises. Several potential approaches have been proposed:
- Targeted Surveillance:This approach involves allowing law enforcement agencies to access encrypted communications only in specific, well-defined circumstances, such as when there is a credible suspicion of CSAM activity. This approach aims to strike a balance between privacy protection and law enforcement needs.
- Hashing and Metadata Analysis:Instead of decrypting content, law enforcement could rely on hashing algorithms and metadata analysis to identify potentially illegal content. This approach could provide a balance between privacy protection and the ability to detect CSAM.
- Collaboration and Information Sharing:Enhanced collaboration between technology companies, law enforcement agencies, and child protection organizations is crucial for combating CSAM. This could involve sharing best practices, developing new technologies, and creating a more effective framework for detecting and reporting illegal content.
International Perspectives on Encryption and Child Safety
The debate surrounding encryption and child safety is not confined to the UK. Various countries around the world grapple with the same complex issue, seeking to strike a balance between protecting children from online harm and upholding individual privacy rights.
This section explores the stances of different nations on encryption and child safety, comparing their approaches to balancing privacy and protection, and examining the potential for international collaboration in addressing these issues.
Different Approaches to Balancing Privacy and Child Protection
The approaches to balancing privacy and child protection in the context of encryption vary significantly across countries. Some countries, like the UK, advocate for backdoors or access mechanisms to encrypted communications for law enforcement to investigate child sexual abuse material (CSAM).
Others, like Germany, prioritize strong encryption and argue that backdoors weaken security for everyone and could be exploited by malicious actors. The following examples illustrate these different approaches:
- United States: The US has adopted a mixed approach. While the government has expressed concerns about encryption’s impact on child safety, it has also acknowledged the importance of strong encryption for national security and economic competitiveness. The US has not explicitly endorsed backdoors, but has pushed for technology companies to provide assistance in investigations involving CSAM.
- European Union: The EU’s approach is also evolving. The General Data Protection Regulation (GDPR) emphasizes data privacy and restricts government access to encrypted data. However, the EU has also proposed regulations requiring tech companies to proactively detect and remove CSAM, which could potentially require some form of access to encrypted content.
- Australia: Australia has adopted a more aggressive stance, enacting legislation requiring tech companies to provide access to encrypted data for law enforcement. This approach has faced criticism from privacy advocates, who argue that it undermines encryption’s security and could have unintended consequences.
Potential for International Collaboration
The complexities of encryption and child safety demand international cooperation. While countries may have differing approaches, there is a shared interest in protecting children online. International collaboration could focus on several key areas:
- Sharing best practices: Countries could exchange information on effective strategies for combating CSAM, including non-intrusive methods like proactive detection and removal technologies.
- Developing common standards: International standards could be established for encryption and child safety, ensuring that both privacy and security are adequately addressed.
- Promoting research and development: Collaboration could support research and development of technologies that can effectively detect and prevent CSAM without compromising encryption’s security.
Technological Solutions and Alternatives: Uk Targets Meta Encryption Plans Child Sexual Abuse Concerns
The debate surrounding encryption and child sexual abuse material (CSAM) highlights a complex challenge: balancing privacy with safety. While end-to-end encryption safeguards user communications, it also presents a potential haven for illegal activities. This section explores potential technological solutions that could mitigate these risks while preserving privacy, and examines alternative approaches to combating CSAM.
Technological Solutions
Finding technological solutions that effectively address the risks associated with encryption while maintaining user privacy is a crucial endeavor. This requires innovative approaches that balance security and privacy.
- Client-Side Scanning:This approach involves scanning user devices for CSAM before it is encrypted. This method raises significant privacy concerns, as it could potentially expose private data and be vulnerable to false positives. However, some proponents argue that it could be a valuable tool for identifying and preventing the spread of CSAM.
To mitigate privacy concerns, such systems would need to be carefully designed with strong safeguards against abuse and misuse.
- Metadata Analysis:Metadata, such as the sender and receiver of a message, the time it was sent, and the file size, can be analyzed to identify suspicious patterns. This approach does not require decryption of the message content itself and can be used to detect potential CSAM sharing.
However, it is important to note that metadata analysis can be used to infer sensitive information about users, and its effectiveness in detecting CSAM may be limited.
- Zero-Trust Architecture:This approach assumes that no user or device can be trusted by default. It involves implementing robust authentication and authorization mechanisms, as well as continuous monitoring and threat detection. By implementing a zero-trust architecture, platforms can better protect themselves against unauthorized access and malicious activity, potentially reducing the risk of CSAM being shared.
- Federated Learning:This technique allows multiple devices to collaboratively train a machine learning model without sharing their individual data. This could be used to detect CSAM without requiring access to the content itself. For example, devices could share encrypted representations of their data, enabling the model to learn patterns without compromising individual privacy.
Alternative Approaches, Uk targets meta encryption plans child sexual abuse concerns
Beyond technological solutions, there are alternative approaches to combating CSAM that do not rely solely on encryption. These approaches address the underlying issues that contribute to the problem.
- Education and Prevention:Educating children and parents about online safety, responsible online behavior, and the dangers of CSAM is crucial. This includes teaching them how to identify and report potential abuse.
- Strengthening Law Enforcement:Improving law enforcement capabilities to effectively investigate and prosecute CSAM offenders is essential. This includes providing law enforcement with the necessary tools and resources to combat online crime.
- Collaborative Efforts:Engaging in collaborative efforts between tech companies, law enforcement agencies, and child protection organizations is crucial. This includes sharing information, best practices, and resources to combat CSAM effectively.
Hypothetical System
Imagine a system that utilizes a combination of technological solutions and alternative approaches to balance privacy and security. This hypothetical system could incorporate:
- Client-Side Scanning with Enhanced Privacy Safeguards:This could involve using a trusted execution environment (TEE) to isolate the scanning process, ensuring that only authorized entities have access to the data. Additionally, a system of independent audits could be implemented to ensure the integrity and effectiveness of the scanning process.
- Metadata Analysis with Privacy-Preserving Techniques:This could involve using differential privacy, a technique that adds noise to data to protect individual privacy while still allowing for meaningful analysis.
- Federated Learning for CSAM Detection:This could be used to train models that can detect CSAM without requiring access to the content itself. This approach would ensure that user data remains private while still enabling effective detection of illegal content.
- Proactive Content Moderation:Platforms could use a combination of machine learning algorithms and human review to proactively identify and remove CSAM. This would require a careful balance between automation and human oversight to ensure accuracy and prevent censorship.
- Enhanced Reporting Mechanisms:Platforms could implement user-friendly reporting mechanisms that make it easier for users to report suspected CSAM. This could include providing clear instructions and support to users who are unsure about how to report abuse.
Future Implications and Potential Outcomes
The potential impact of Meta’s encryption plans on online safety and privacy is a complex and multifaceted issue with far-reaching consequences. This section explores the potential implications for both users and law enforcement agencies, examining the key stakeholders involved and their respective positions in this ongoing debate.
Impact on Online Safety and Privacy
The potential impact of Meta’s encryption plans on online safety and privacy is a complex issue with both potential benefits and risks.
- Enhanced Privacy:End-to-end encryption would make it more difficult for Meta to access user data, potentially improving user privacy and security. Users would have greater control over their information, making it harder for third parties, including governments, to intercept or access their communications.
- Reduced Surveillance:Encryption could hinder the ability of law enforcement agencies to monitor online activity, potentially making it more difficult to investigate criminal activities like child sexual abuse material (CSAM). However, it is important to note that encryption does not create a “black box” for law enforcement, and they can still use other methods to investigate crimes.
- Increased Security:Encryption can make it more difficult for malicious actors to access and exploit user data, potentially reducing the risk of data breaches and cyberattacks. This could be particularly beneficial for users who are vulnerable to online harassment or threats.
Impact on Law Enforcement Agencies
The potential impact of Meta’s encryption plans on law enforcement agencies is a subject of intense debate. While encryption can enhance user privacy and security, it can also make it more difficult for law enforcement to investigate criminal activities.
- Challenges in Investigating Crimes:Encryption can hinder law enforcement’s ability to access evidence in online investigations, potentially making it more difficult to prosecute crimes like child sexual abuse, terrorism, and drug trafficking. However, it’s important to note that law enforcement agencies still have access to other investigative tools, and encryption does not completely prevent them from gathering evidence.
- Need for Balance:Law enforcement agencies argue that encryption should not come at the expense of public safety. They advocate for mechanisms that allow for lawful access to encrypted data in specific circumstances, such as when there is a warrant or a compelling need for evidence.
- Technological Solutions:Law enforcement agencies are exploring technological solutions to address the challenges posed by encryption, such as “lawful intercept” mechanisms that allow for controlled access to encrypted data with proper authorization. These solutions aim to balance the need for privacy with the need for public safety.
Key Stakeholders and Their Positions
The debate surrounding Meta’s encryption plans involves various stakeholders with differing perspectives.
- Meta:Meta advocates for strong encryption as a fundamental principle of online privacy and security. They argue that encryption protects users from unauthorized access and enhances their control over their data.
- Law Enforcement Agencies:Law enforcement agencies express concerns about the potential impact of encryption on their ability to investigate criminal activities. They advocate for mechanisms that allow for lawful access to encrypted data in specific circumstances.
- Privacy Advocates:Privacy advocates support strong encryption as a crucial safeguard against government surveillance and corporate data collection. They argue that encryption empowers individuals to control their data and protect their privacy.
- Child Safety Organizations:Child safety organizations express concerns about the potential for encrypted platforms to facilitate child sexual abuse. They advocate for measures that balance privacy with the need to protect children online.
- Technology Companies:Technology companies, beyond Meta, are also engaged in the debate, with some supporting strong encryption and others expressing concerns about the potential impact on their business models and their ability to combat illegal activity.