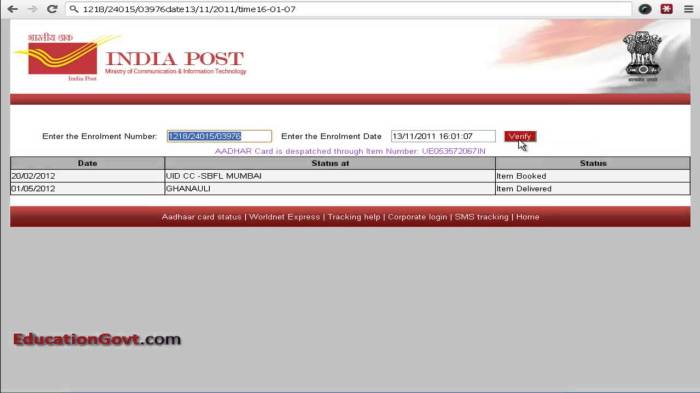
Online accounts could be verified using indian governments unique id project aadhaar – Online accounts could be verified using Indian government’s unique ID project Aadhaar, a system that has sparked debate and raised concerns about privacy and security. Aadhaar, a 12-digit biometric identifier, has become a crucial tool for streamlining various government services and facilitating online transactions in India.
This post explores the intricacies of Aadhaar-based verification, examining its advantages, drawbacks, and the future implications for the digital landscape.
The Aadhaar system relies on biometric authentication, utilizing fingerprints and iris scans to verify an individual’s identity. This method offers a higher level of security compared to traditional methods, making it appealing for online account verification. However, concerns regarding data security and privacy have been raised, prompting a cautious approach towards the widespread adoption of Aadhaar for online verification.
Aadhaar’s Role in Online Account Verification
Aadhaar, India’s unique identification project, has emerged as a powerful tool for verifying identities in the digital realm. This biometric-based system offers a secure and efficient means of verifying online accounts, streamlining processes and enhancing security.
Advantages of Using Aadhaar for Online Account Verification
Aadhaar’s use in online account verification offers several advantages, contributing to a more secure and convenient digital experience.
- Enhanced Security:Aadhaar’s biometric authentication, involving fingerprint or iris scans, significantly reduces the risk of identity theft and fraud. The unique and verifiable nature of Aadhaar data strengthens the security of online accounts, protecting users from unauthorized access.
- Simplified Verification Process:Aadhaar verification eliminates the need for traditional document-based verification methods, simplifying the account creation process. Users can easily verify their identities through a quick and convenient Aadhaar-based authentication process.
- Reduced Fraud:Aadhaar’s robust verification system helps to curb fraudulent activities by preventing the creation of multiple accounts using fake identities. This enhanced security measure contributes to a safer online environment for users.
- Improved User Experience:The streamlined verification process using Aadhaar enhances the user experience, making account creation faster and more convenient. Users can complete the process quickly without the hassle of traditional verification methods.
Security Concerns Associated with Using Aadhaar for Online Verification
While Aadhaar offers significant benefits for online account verification, certain security concerns need to be addressed.
Obtain direct knowledge about the efficiency of 5 things look right e commerce platform business through case studies.
- Data Privacy and Security:The collection and storage of sensitive biometric data raise concerns about privacy and security. Ensuring the protection of Aadhaar data from unauthorized access and misuse is crucial to maintain user trust.
- Potential for Misuse:The widespread use of Aadhaar for online verification raises concerns about potential misuse by entities seeking to gain access to personal information or exploit the system for fraudulent activities. Robust security measures and strict regulations are essential to prevent such misuse.
- Accessibility and Inclusivity:Ensuring that all individuals, including those without access to smartphones or internet connectivity, can benefit from Aadhaar-based verification is crucial. Measures to address accessibility and inclusivity are necessary to avoid digital exclusion.
Technical Aspects of Aadhaar-Based Verification

Aadhaar-based verification, a cornerstone of digital India, leverages a sophisticated technological framework to ensure secure and reliable authentication. This framework encompasses various technical processes, authentication methods, and the strategic utilization of biometric data.
Authentication Methods in Aadhaar Verification
Aadhaar verification utilizes a robust authentication system that combines multiple methods to ensure accuracy and security.
- Offline Verification:This method involves verifying an individual’s identity through physical documents like Aadhaar card or e-Aadhaar. It is primarily used in situations where online access is unavailable or unreliable.
- Online Verification:This method utilizes online platforms to verify an individual’s identity through Aadhaar. It leverages the Aadhaar database to confirm an individual’s details against the provided Aadhaar number. This method is widely used for various online services and transactions.
- Biometric Authentication:This method employs biometric data, such as fingerprints or iris scans, to authenticate an individual’s identity. Biometric authentication adds an extra layer of security and is considered highly reliable.
The Role of Biometric Data in Aadhaar-Based Verification
Biometric data plays a pivotal role in Aadhaar-based verification, enhancing security and accuracy.
- Fingerprint Scanning:Fingerprint scanning involves capturing and analyzing an individual’s fingerprint patterns, which are unique and highly reliable for identification purposes. This method is widely used for authentication in various scenarios, including Aadhaar enrollment and verification.
- Iris Scanning:Iris scanning captures and analyzes the unique patterns in an individual’s iris, the colored part of the eye. This method is considered highly secure and accurate, as iris patterns are extremely complex and unlikely to be replicated. It is used for authentication in situations requiring a higher level of security, such as bank transactions or government services.
Technical Processes Involved in Aadhaar-Based Verification
Aadhaar-based verification involves a series of technical processes that ensure secure and reliable authentication.
- Aadhaar Number Validation:This process involves checking the validity of the provided Aadhaar number against the Aadhaar database. It ensures that the number is genuine and not a fabrication.
- Data Retrieval:Once the Aadhaar number is validated, the system retrieves the corresponding demographic and biometric data from the Aadhaar database. This data is then used for verification purposes.
- Biometric Matching:If biometric authentication is required, the system compares the provided biometric data with the stored data in the Aadhaar database. This process ensures that the individual is who they claim to be.
- Authentication Confirmation:Based on the verification results, the system generates an authentication response, confirming or denying the individual’s identity. This response is typically communicated to the requesting entity.
Impact on User Experience
Aadhaar-based verification has the potential to significantly impact user experience in online accounts. By streamlining the verification process and enhancing security, it can make online interactions more convenient and secure for users.
Ease of Use and Accessibility
The ease of use and accessibility of Aadhaar-based verification systems are crucial for a positive user experience.
- Simplified Verification Process:Aadhaar-based verification simplifies the account verification process, eliminating the need for traditional methods like physical documents or complex procedures. Users can verify their identity quickly and easily using their Aadhaar number and biometric authentication, which is convenient and efficient.
- Wide Accessibility:Aadhaar is widely accessible across India, with a large majority of the population enrolled in the system. This broad accessibility ensures that users can easily verify their identity regardless of their location or socioeconomic background.
- Integration with Existing Platforms:Aadhaar-based verification can be seamlessly integrated with existing online platforms, providing a consistent and familiar experience for users. This integration eliminates the need for users to learn new verification procedures or navigate unfamiliar interfaces.
Comparison with Other Verification Methods
Comparing Aadhaar-based verification with other methods reveals its advantages in terms of user experience.
- Traditional Document Verification:Traditional methods often involve submitting physical documents, which can be time-consuming, inconvenient, and prone to errors. Aadhaar-based verification offers a faster, more efficient, and secure alternative.
- OTP-Based Verification:While OTP-based verification is relatively quick, it can be prone to security risks, such as phishing attacks or unauthorized access to OTPs. Aadhaar-based verification, with its biometric authentication, provides a more robust and secure verification mechanism.
- Knowledge-Based Authentication:Knowledge-based authentication relies on users remembering personal information, which can be challenging or unreliable. Aadhaar-based verification, with its biometric authentication, eliminates the need for users to recall sensitive information.
Privacy and Security Concerns: Online Accounts Could Be Verified Using Indian Governments Unique Id Project Aadhaar
The widespread adoption of Aadhaar for online account verification raises legitimate concerns about the potential impact on individual privacy and the security of sensitive personal information. While the Indian government has implemented measures to safeguard Aadhaar data, the sheer volume of information collected and its potential for misuse necessitates a thorough examination of these concerns.
Potential Privacy Concerns
The use of Aadhaar for online account verification raises several privacy concerns, as it involves the collection and sharing of sensitive personal information with third-party entities. These concerns are particularly relevant in the context of online services, where data breaches and misuse are prevalent.
- Data Sharing and Control:The use of Aadhaar for online account verification implies the sharing of personal information with various entities, potentially without the user’s explicit consent or knowledge. This raises concerns about the control individuals have over their own data and the potential for misuse by third parties.
- Surveillance and Profiling:The linkage of Aadhaar with online accounts can facilitate the creation of detailed profiles about individuals’ online activities and preferences. This information can be used for targeted advertising, surveillance, and profiling, potentially leading to discrimination or prejudice.
- Lack of Transparency and Accountability:The process of data sharing and usage by third parties may lack transparency and accountability, making it difficult for individuals to understand how their data is being used or to challenge its misuse.
Security Measures for Aadhaar Data
To mitigate these concerns, the Indian government has implemented several security measures to protect Aadhaar data during verification processes. These measures aim to ensure the confidentiality, integrity, and availability of Aadhaar information.
- Encryption and Secure Transmission:Aadhaar data is encrypted during transmission and storage, making it difficult for unauthorized individuals to access or modify it.
- Two-Factor Authentication:Aadhaar-based verification typically involves two-factor authentication, requiring both a biometric authentication (fingerprint or iris scan) and a one-time password (OTP) sent to the registered mobile number. This adds an extra layer of security to the verification process.
- Auditing and Monitoring:Regular audits and monitoring of Aadhaar systems are conducted to detect and prevent unauthorized access or data breaches.
Risks of Data Breaches and Misuse, Online accounts could be verified using indian governments unique id project aadhaar
Despite the security measures in place, the potential for data breaches and misuse of Aadhaar information remains a significant concern.
- Data Breaches:Data breaches in online services can expose Aadhaar data to unauthorized individuals, potentially leading to identity theft, financial fraud, and other malicious activities.
- Misuse by Third Parties:Even if data breaches are prevented, there is a risk that third parties might misuse Aadhaar information for unauthorized purposes, such as profiling, discrimination, or targeted marketing.
- Lack of Adequate Data Protection Laws:The current data protection laws in India may not be comprehensive enough to address the specific challenges posed by Aadhaar-based verification.
Regulatory Framework and Legal Considerations
The use of Aadhaar for online verification, while offering convenience and efficiency, raises significant legal and ethical considerations. It’s crucial to understand the legal framework governing this practice and the ethical implications involved.The legal framework governing Aadhaar’s use for online verification is primarily based on the Aadhaar Act, 2016, and the accompanying rules and regulations.
This legislation Artikels the permissible uses of Aadhaar, the rights of individuals, and the responsibilities of entities using Aadhaar for verification.
Aadhaar Act and Regulations
The Aadhaar Act, 2016, provides the legal basis for the use of Aadhaar for various purposes, including online verification. The Act emphasizes the importance of privacy and security, outlining specific regulations for data protection and ensuring responsible use of Aadhaar data.
The Act also establishes the Unique Identification Authority of India (UIDAI) as the regulatory body responsible for overseeing Aadhaar-related matters.
Ethical Implications of Aadhaar-Based Verification
The use of Aadhaar for online verification raises ethical concerns, particularly regarding privacy and security. Critics argue that the collection and use of sensitive personal information, such as biometric data, could lead to privacy violations and potential misuse. The potential for data breaches and unauthorized access to Aadhaar data also raises concerns about the security of this system.
Role of Government Agencies and Regulatory Bodies
The UIDAI plays a crucial role in overseeing Aadhaar-based verification. It sets guidelines for entities using Aadhaar for verification, ensuring compliance with the Aadhaar Act and related regulations. The UIDAI also monitors the use of Aadhaar to prevent misuse and protect individuals’ privacy.
Privacy and Security Concerns
The use of Aadhaar for online verification raises significant privacy and security concerns. These concerns include:
- Data Breaches:The possibility of data breaches, where unauthorized individuals gain access to sensitive Aadhaar data, poses a significant risk.
- Unauthorized Access:Concerns exist about unauthorized access to Aadhaar data by entities or individuals without proper authorization.
- Surveillance and Profiling:The use of Aadhaar for online verification could lead to the creation of extensive profiles of individuals, raising concerns about government surveillance and potential discrimination.
Data Protection and Security Measures
To address these concerns, the UIDAI has implemented various data protection and security measures, including:
- Data Encryption:Aadhaar data is encrypted to prevent unauthorized access and ensure confidentiality.
- Secure Authentication:Secure authentication mechanisms are employed to verify the identity of users accessing Aadhaar data.
- Regular Audits:Regular audits are conducted to ensure compliance with security standards and data protection regulations.
Future Prospects and Potential Applications
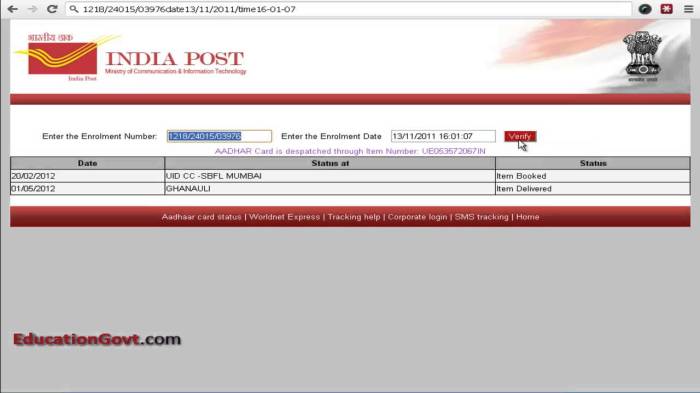
The potential of Aadhaar-based verification extends far beyond simply verifying online accounts. Its ability to securely and reliably authenticate individuals opens up a vast array of possibilities for transforming various sectors of the Indian economy. This technology has the potential to revolutionize how we interact with government services, financial institutions, and even the private sector.
Impact on the Digital Economy
Aadhaar-based verification can significantly impact the digital economy by fostering trust and transparency in online transactions. This can be achieved by:
- Increased financial inclusion:By enabling secure and reliable identification, Aadhaar-based verification can facilitate access to financial services for millions of previously unbanked individuals, driving financial inclusion and economic growth.
- Reduced fraud and identity theft:The unique and verifiable nature of Aadhaar can significantly reduce fraud and identity theft in online transactions, creating a safer and more secure digital environment.
- Enhanced e-commerce adoption:With increased trust and security, Aadhaar-based verification can encourage more people to participate in e-commerce, leading to increased economic activity and job creation.
Further Development and Improvement
While Aadhaar-based verification offers immense potential, it is crucial to address certain aspects for further development and improvement:
- Privacy and security concerns:Continuously enhancing security measures and implementing robust data protection protocols are essential to maintain user trust and ensure the responsible use of Aadhaar data.
- Accessibility and inclusivity:Ensuring that Aadhaar-based verification is accessible to all citizens, including those in remote areas and with disabilities, is crucial for its widespread adoption.
- User experience:Streamlining the verification process and making it user-friendly is essential for encouraging widespread adoption and maximizing its benefits.