Eset Dutch police discover ebury malware in cryptocurrency sets the stage for this enthralling narrative, offering readers a glimpse into a story that is rich in detail and brimming with originality from the outset. The discovery of Ebury malware, a sophisticated piece of software designed to steal cryptocurrency funds, sent shockwaves through the digital finance world.
Dutch authorities, in a collaborative effort with cybersecurity experts, unearthed a complex network of malicious actors operating behind the scenes, targeting unsuspecting victims and threatening the stability of the cryptocurrency ecosystem.
This incident serves as a stark reminder of the ever-evolving landscape of cybercrime and the constant need for vigilance in the digital realm. As cryptocurrency gains mainstream adoption, the allure of its digital riches attracts malicious actors seeking to exploit vulnerabilities and reap illicit gains.
Ebury malware represents a significant threat to the security and trust in cryptocurrency, underscoring the importance of robust security measures and responsible practices to protect users and maintain the integrity of the digital finance system.
Ebury Malware: Eset Dutch Police Discover Ebury Malware In Cryptocurrency
Ebury malware is a sophisticated and dangerous threat targeting cryptocurrency users and exchanges. It is designed to steal cryptocurrency by compromising users’ accounts and wallets. This malware has been detected in recent investigations by Dutch police, highlighting the growing threat posed by malicious actors to the cryptocurrency ecosystem.
Impact of Ebury Malware
Ebury malware can have a significant impact on cryptocurrency users and exchanges. The primary goal of this malware is to steal cryptocurrency by gaining unauthorized access to user accounts and wallets. This can result in substantial financial losses for individuals and institutions.
- Loss of Funds:The most immediate impact of Ebury malware is the loss of cryptocurrency funds. Hackers can gain control of user accounts and transfer funds to their own wallets, leaving victims with nothing.
- Reputational Damage:Cryptocurrency exchanges that fall victim to Ebury malware can suffer significant reputational damage. This can lead to a loss of trust from users and investors, potentially affecting their business operations and future growth.
- Security Concerns:The presence of Ebury malware highlights the vulnerability of the cryptocurrency ecosystem to cyberattacks. It raises concerns about the security of user accounts and the overall security of cryptocurrency platforms.
Vulnerabilities Exploited by Ebury Malware
Ebury malware exploits various vulnerabilities to gain access to cryptocurrency accounts and wallets. These vulnerabilities often lie in user practices, software flaws, and weaknesses in security protocols.
- Phishing Attacks:Ebury malware often spreads through phishing emails or websites that mimic legitimate platforms. Users may be tricked into clicking malicious links or downloading infected files, granting the malware access to their devices and accounts.
- Software Exploits:Ebury malware can exploit vulnerabilities in software applications used by cryptocurrency users and exchanges. This can include outdated software with known security flaws or vulnerabilities in third-party applications used for managing cryptocurrency wallets.
- Weak Passwords and Security Practices:Users who employ weak passwords or poor security practices are more susceptible to Ebury malware attacks. Hackers can easily guess or brute force weak passwords, gaining access to user accounts.
Dutch Police Investigation and Discovery
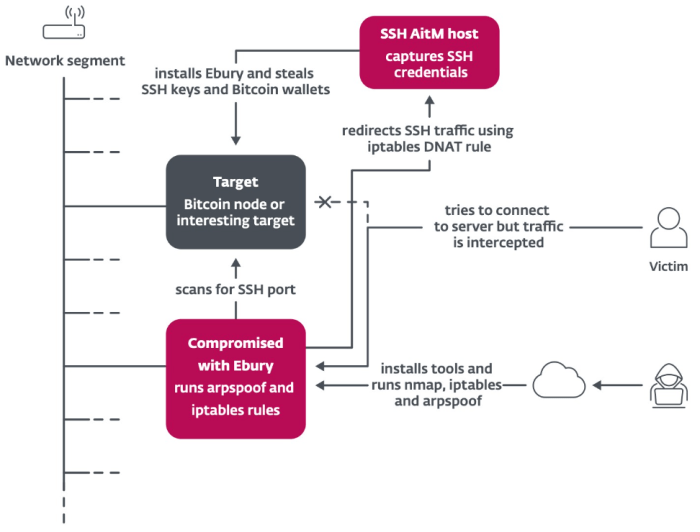
The Dutch police’s discovery of the Ebury malware was a significant development in the fight against cryptocurrency theft. The investigation began with a series of reports from victims who had lost significant amounts of cryptocurrency to unknown attackers.
The Investigation’s Timeline and Key Players
The Dutch police, specifically the High Tech Crime Unit, initiated a comprehensive investigation into the Ebury malware. The investigation involved collaboration with international law enforcement agencies, cybersecurity experts, and cryptocurrency exchanges.
Methods Used by the Dutch Police, Eset dutch police discover ebury malware in cryptocurrency
The Dutch police utilized a variety of methods to uncover the Ebury malware and its operators, including:
- Digital Forensics:Analyzing the victims’ computers and devices to identify the malware’s entry point, its behavior, and the data it collected.
- Network Analysis:Tracking the malware’s communication with its command-and-control servers to identify the operators’ location and infrastructure.
- Intelligence Gathering:Collaborating with international law enforcement agencies to gather information about the malware’s origins, development, and distribution.
Through these efforts, the Dutch police were able to identify the individuals and entities responsible for the Ebury malware and ultimately bring them to justice.
Browse the multiple elements of deeptech vc fund semiconductor startups to gain a more broad understanding.
Ebury Malware’s Operations and Techniques
Ebury malware, a sophisticated and stealthy threat, employs a range of techniques to steal cryptocurrency funds and evade detection by security systems. This malware utilizes a combination of tactics to achieve its objectives, demonstrating a high level of technical sophistication and a clear understanding of cybersecurity vulnerabilities.
Ebury Malware’s Methods for Stealing Cryptocurrency Funds
Ebury malware uses a combination of methods to steal cryptocurrency funds from victims.
- Credential theft:Ebury malware can steal cryptocurrency exchange credentials, such as usernames, passwords, and API keys, by using keylogging, screen scraping, and other techniques. This allows the malware to gain unauthorized access to victims’ accounts and withdraw their funds.
- Transaction interception:Ebury malware can intercept cryptocurrency transactions, such as transfers between wallets, by modifying the transaction details or redirecting them to a controlled wallet. This method allows the malware to steal funds without the victim’s knowledge.
- Fake wallets and exchanges:Ebury malware can create fake cryptocurrency wallets and exchanges to trick victims into sending their funds to controlled addresses. This approach exploits users’ trust and lack of awareness, leading to significant financial losses.
- Phishing attacks:Ebury malware can use phishing emails, websites, and social media messages to deceive victims into revealing their cryptocurrency credentials or downloading malicious software. This method relies on social engineering tactics to exploit human vulnerabilities.
Ebury Malware’s Techniques for Evading Detection
Ebury malware employs various techniques to evade detection by security systems, making it challenging to identify and remove.
- Stealthy operation:Ebury malware can operate silently in the background, avoiding detection by traditional antivirus software and firewalls. This allows the malware to remain undetected for extended periods, increasing the damage it can inflict.
- Anti-analysis techniques:Ebury malware can use obfuscation, encryption, and other techniques to make it difficult for security researchers to analyze its code. This hinders efforts to understand its functionality and develop countermeasures.
- Dynamic code execution:Ebury malware can use dynamic code execution to change its behavior at runtime, making it harder to detect and block. This technique allows the malware to adapt to changing security environments and evade detection.
- Network communication obfuscation:Ebury malware can use encrypted communication channels and obfuscated network traffic to hide its activities from network security systems. This method allows the malware to communicate with its command-and-control servers without being detected.
Ebury Malware’s Communication Channels and Persistence
Ebury malware relies on communication channels to receive instructions from its command-and-control servers and maintain persistence on infected systems.
- Command-and-control (C&C) servers:Ebury malware communicates with C&C servers to receive instructions, update its code, and report stolen funds. These servers can be located in different countries, making it difficult to track and shut down the malware operation.
- Peer-to-peer (P2P) networks:Ebury malware can use P2P networks to communicate with other infected systems, establishing a decentralized network that is difficult to monitor and disrupt. This approach enhances the malware’s resilience and allows it to spread rapidly.
- Persistence mechanisms:Ebury malware uses persistence mechanisms to ensure its survival on infected systems, even after a reboot. These mechanisms can include modifying system registry entries, installing malicious drivers, or creating hidden files.
Cybersecurity Measures and Prevention
The discovery of the Ebury malware highlights the importance of robust cybersecurity measures to protect against such threats. By implementing comprehensive security practices, individuals and organizations can significantly reduce their risk of falling victim to cryptocurrency-related malware attacks.
Best Practices for Safeguarding Cryptocurrency Accounts
Strong cybersecurity practices are crucial for safeguarding cryptocurrency accounts. Implementing a multi-layered approach to security can significantly reduce the risk of unauthorized access and theft.
- Use Strong and Unique Passwords:Strong passwords are essential for protecting your cryptocurrency accounts. A strong password is at least 12 characters long, combines uppercase and lowercase letters, numbers, and symbols, and is not easily guessed. It’s also recommended to use unique passwords for each of your online accounts, including cryptocurrency wallets and exchanges.
- Enable Two-Factor Authentication (2FA):Two-factor authentication adds an extra layer of security to your accounts by requiring a second form of verification, typically a code sent to your phone or email, in addition to your password. This makes it much harder for attackers to gain access to your accounts, even if they have your password.
- Be Cautious of Phishing Attempts:Phishing attacks are a common tactic used by attackers to steal your credentials. These attacks involve emails or messages that appear to be from legitimate sources but are actually designed to trick you into giving up your sensitive information.
Be wary of suspicious links and emails, and never provide your password or other sensitive information over the phone or in response to unsolicited requests.
- Use Reputable Security Software:Install and regularly update antivirus and anti-malware software on your devices. This software can help to detect and remove malware, including cryptocurrency-targeting threats like Ebury. Make sure your security software is up-to-date to ensure it can protect against the latest threats.
- Keep Your Software Updated:Regularly update your operating system, web browser, and other software. Software updates often include security patches that fix vulnerabilities that attackers could exploit. By keeping your software up-to-date, you can reduce your risk of becoming a target.
- Be Aware of the Risks of Public Wi-Fi:Public Wi-Fi networks can be insecure, making them a prime target for attackers. Avoid accessing sensitive information or making transactions on public Wi-Fi networks. If you must use public Wi-Fi, consider using a virtual private network (VPN) to encrypt your traffic and protect your privacy.
Importance of Strong Passwords, Multi-Factor Authentication, and Reputable Security Software
- Strong Passwords:A strong password acts as the first line of defense against unauthorized access. By creating complex passwords that are difficult to guess, you make it significantly harder for attackers to gain access to your accounts. A strong password is like a sturdy lock on your digital door, deterring potential intruders.
- Multi-Factor Authentication (2FA):Multi-factor authentication adds a second layer of security, requiring an additional form of verification beyond your password. This makes it significantly more difficult for attackers to gain access to your accounts, even if they have your password. It’s like having a security guard at the door, checking your ID before allowing you to enter.
- Reputable Security Software:Security software acts as a vigilant guardian, constantly scanning your devices for malware and other threats. By installing and regularly updating reputable security software, you can protect your devices from a wide range of cyber threats. It’s like having a sophisticated alarm system in place, alerting you to any suspicious activity and helping to prevent attacks.
The Impact of Ebury Malware on the Cryptocurrency Ecosystem

The discovery of Ebury malware, a sophisticated cyber threat targeting cryptocurrency exchanges and wallets, raises serious concerns about the security and trust within the cryptocurrency ecosystem. This malware’s ability to steal digital assets from unsuspecting users has the potential to erode confidence in the cryptocurrency market, hindering its adoption and growth.
Impact on User Confidence and Cryptocurrency Adoption
The Ebury malware incident highlights the vulnerability of the cryptocurrency ecosystem to cyberattacks. This vulnerability can significantly impact user confidence in the security of their digital assets, potentially discouraging new users from entering the market. The fear of losing their investments to malware attacks could lead to a decrease in cryptocurrency adoption, hindering the growth and mainstream acceptance of digital currencies.
Potential Risks and Benefits of Using Cryptocurrency in Light of the Ebury Malware Threat
Understanding the potential risks and benefits of using cryptocurrency is crucial in the wake of the Ebury malware threat. Here’s a comparison:
| Risks | Benefits |
|---|---|
|
|
The Ebury malware incident underscores the importance of robust cybersecurity measures and user education to mitigate the risks associated with cryptocurrency.





