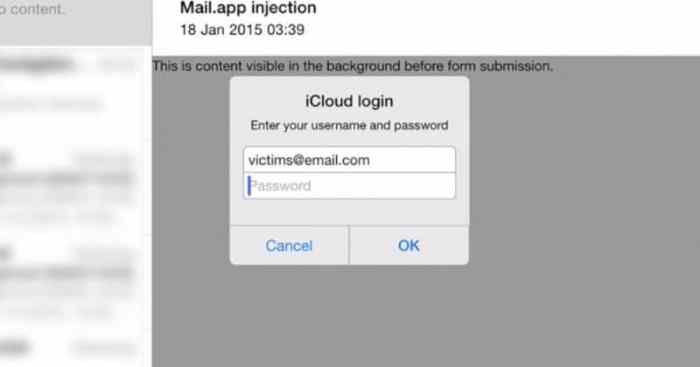
Bug in ios mail app lets hackers send fake password collector as a pop up notification – iOS Mail App Bug Lets Hackers Steal Passwords: Imagine opening your email and seeing a pop-up asking for your password. This isn’t a scene from a sci-fi thriller, but a real threat facing iOS users. A recent bug in the iOS Mail app allows hackers to send fake password collection pop-ups, disguised as legitimate notifications, directly to your device.
This vulnerability could potentially lead to identity theft and financial fraud, making it crucial to understand the risks and take steps to protect yourself.
The bug exploits a weakness in the way the iOS Mail app handles notifications. Hackers can craft malicious emails that trigger fake pop-ups, mimicking official login prompts. These fake prompts often appear as a simple notification, prompting you to enter your password or other sensitive information.
Once you submit your details, the hackers have access to your accounts, potentially compromising your online security.
The Bug
The iOS Mail app recently had a vulnerability that allowed hackers to send fake password collector pop-up notifications, potentially tricking users into revealing their sensitive information. This exploit targeted a flaw in the way the app handled notifications, enabling attackers to disguise malicious content as legitimate system messages.
Understanding the Vulnerability
This vulnerability stemmed from a weakness in the iOS Mail app’s handling of notifications. Hackers exploited this flaw by sending specially crafted emails that triggered the display of a fake pop-up notification. This notification, designed to mimic a genuine system message, would request the user to enter their password or other sensitive data.
Discover how saudi arabia unveils designs for the line vision a 170km long 200m wide city has transformed methods in this topic.
The Exploit Method
The exploit involved the following steps:
- Hackers sent emails containing a specific type of code that tricked the iOS Mail app into displaying a pop-up notification.
- This notification, designed to resemble a legitimate system message, would ask the user to provide their password or other sensitive information.
- If the user unknowingly entered their credentials, the hackers could intercept this information and potentially gain access to their accounts.
Impact of the Bug
This bug, while addressed, had the potential to significantly impact iOS users. Hackers could have exploited it to gain access to sensitive information and potentially compromise user accounts.
Potential Consequences for iOS Users
The consequences of falling victim to this exploit could have been severe. Hackers could have used this vulnerability to:
- Steal user credentials, including passwords and login information for various online accounts.
- Gain access to personal data stored on the device, such as contacts, emails, photos, and financial information.
- Install malicious software on the user’s device, enabling further exploitation and data theft.
Examples of Information Hackers Could Gain Access to
The information hackers could have accessed includes:
- Email accounts: Hackers could gain access to email accounts and steal personal and professional correspondence, potentially compromising sensitive information such as financial statements or confidential work documents.
- Social media accounts: Hackers could access social media accounts, potentially leading to identity theft, reputational damage, or the spread of misinformation.
- Online banking accounts: Hackers could access online banking accounts and steal financial information, leading to financial fraud and significant financial losses.
- Other online accounts: Hackers could access any online accounts that the user has logged into on their device, potentially compromising a wide range of personal and professional information.
Potential for Identity Theft and Financial Fraud
The stolen information could have been used for identity theft and financial fraud.
- Identity theft: Hackers could use the stolen information to create fake identities, open credit cards, or obtain loans in the victim’s name, potentially damaging the victim’s credit score and financial reputation.
- Financial fraud: Hackers could use stolen financial information to make unauthorized purchases, withdraw funds from bank accounts, or commit other financial crimes, resulting in significant financial losses for the victim.
User Safety and Prevention
This bug, while potentially dangerous, can be mitigated with a few simple steps and a focus on good security practices. Understanding the potential risks and implementing preventative measures is crucial to safeguarding your data.
Identifying Suspicious Pop-up Notifications
It’s essential to be vigilant when interacting with pop-up notifications on your iOS device. Here’s how to identify suspicious notifications:
- Unfamiliar Sender:If the pop-up notification comes from an unknown or unexpected source, it’s a red flag. Legitimate notifications typically originate from familiar apps or services you use.
- Urgent Tone:Notifications that use urgent language, like “Immediate action required” or “Your account is compromised,” are often attempts to scare you into clicking. Take your time and verify the information.
- Request for Personal Information:Be wary of pop-ups that ask for sensitive information like your passwords, credit card details, or social security number. Legitimate apps rarely request such information through pop-ups.
- Unnatural Appearance:If the pop-up notification looks different from other system notifications, or if its design seems off, it could be a fake. Pay attention to the font, color, and overall layout.
Preventing Access to Sensitive Information
Protecting your passwords and sensitive information is paramount. Here are some security best practices:
- Strong Passwords:Use strong passwords that are at least 12 characters long and include a combination of uppercase and lowercase letters, numbers, and symbols. Avoid using easily guessable information like your name, birthdate, or pet’s name.
- Two-Factor Authentication (2FA):Enable 2FA for all your important accounts. This adds an extra layer of security by requiring you to enter a code from your phone or email in addition to your password when logging in.
- Password Manager:Use a reputable password manager to store your passwords securely. Password managers generate strong passwords, encrypt them, and allow you to access them from any device.
- Be Cautious of Links:Don’t click on links in suspicious emails or pop-up notifications. Always verify the legitimacy of the link before clicking.
- Keep Your Software Updated:Regularly update your iOS device and apps. Software updates often include security patches that fix vulnerabilities and protect against potential threats.
Apple’s Response and Patching: Bug In Ios Mail App Lets Hackers Send Fake Password Collector As A Pop Up Notification
Apple, known for its commitment to user privacy and security, responded swiftly to the discovered bug in its iOS Mail app. The company acknowledged the vulnerability and took immediate steps to address it, demonstrating its dedication to protecting user data.
Timeline of Vulnerability Discovery, Disclosure, and Patch Release
Apple’s process for handling security vulnerabilities is a multi-stage process that prioritizes user safety and responsible disclosure. The timeline for this specific bug is an illustration of this approach:
- Discovery:The bug was initially discovered by a security researcher who followed responsible disclosure practices.
- Disclosure:The researcher contacted Apple, providing details of the vulnerability.
- Analysis and Patch Development:Apple’s security team thoroughly analyzed the bug and developed a patch to address it.
- Patch Release:Apple released a security update for iOS, which included the fix for the vulnerability. This update was distributed to all eligible devices.
Apple’s Approach to Security Vulnerabilities, Bug in ios mail app lets hackers send fake password collector as a pop up notification
Apple prioritizes security in its products and has a well-defined process for handling vulnerabilities:
- Responsible Disclosure:Apple encourages security researchers to report vulnerabilities responsibly by providing details to Apple’s security team.
- Bug Bounty Program:Apple offers financial rewards to researchers who discover and report vulnerabilities in its products, incentivizing responsible disclosure.
- Regular Security Updates:Apple regularly releases security updates for its products, including iOS, to address vulnerabilities and improve security.
- Security Research and Development:Apple invests heavily in security research and development to proactively identify and mitigate potential vulnerabilities.
The Future of iOS Security
This recent bug in the iOS Mail app highlights a critical need for enhanced security measures in Apple’s mobile operating system. While Apple has a reputation for prioritizing security, this incident demonstrates that even the most robust systems are susceptible to vulnerabilities.
Moving forward, iOS security must adapt to the evolving threat landscape and embrace a more proactive approach to protect users.
Strengthening iOS Security Protocols
The implications of this bug underscore the importance of continuously refining iOS security protocols. Here are several potential improvements that could be implemented:
- Enhanced Sandboxing:This involves isolating applications and their data from each other, minimizing the impact of potential exploits. More robust sandboxing mechanisms could prevent malicious apps from accessing sensitive information or compromising the system.
- Improved Vulnerability Detection:Apple should invest in more sophisticated vulnerability detection and analysis tools to identify and patch security flaws proactively. This could involve employing automated vulnerability scanning, fuzz testing, and advanced code analysis techniques.
- Real-Time Threat Monitoring:Implementing real-time threat monitoring systems would enable Apple to detect and respond to emerging threats in a timely manner. This could involve analyzing user behavior, network traffic, and app activity to identify suspicious patterns and potential attacks.
User Education and Awareness
User education plays a crucial role in bolstering iOS security. Educating users about common security threats and best practices can empower them to protect themselves against vulnerabilities:
- Phishing Awareness:Users need to be made aware of phishing attempts, which often involve fake emails or messages designed to trick users into revealing sensitive information. Educating users to identify suspicious links, emails, and pop-up messages is essential.
- Password Management:Strong passwords are crucial for protecting user accounts. Encouraging users to adopt robust passwords and using a password manager to securely store them can significantly enhance security.
- App Security:Users should be educated about the importance of downloading apps from trusted sources, such as the App Store, and keeping their apps updated to receive the latest security patches. This helps to minimize the risk of installing malicious apps.