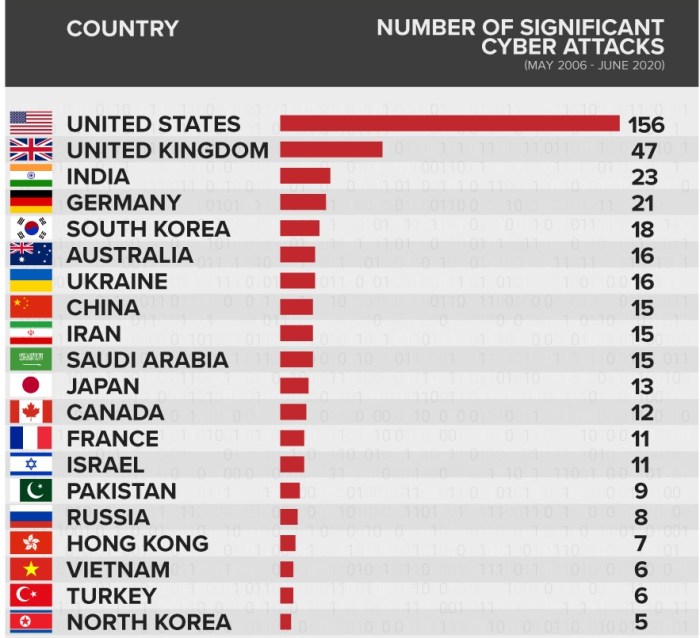
Europe worlds most targeted region for cyberattacks – Europe: The World’s Most Targeted Region for Cyberattacks sets the stage for this enthralling narrative, offering readers a glimpse into a story that is rich in detail and brimming with originality from the outset. The continent’s unique blend of economic prosperity, advanced technology, and complex political landscape makes it a prime target for cybercriminals, nation-state actors, and other malicious entities.
From sophisticated phishing campaigns to crippling ransomware attacks, the threat landscape in Europe is constantly evolving. The impact of these cyberattacks extends far beyond financial losses, affecting critical infrastructure, disrupting essential services, and undermining public trust. This blog delves into the reasons behind Europe’s vulnerability, explores the types of cyberattacks it faces, and examines the strategies being implemented to combat this growing threat.
Europe: A Prime Target for Cyberattacks
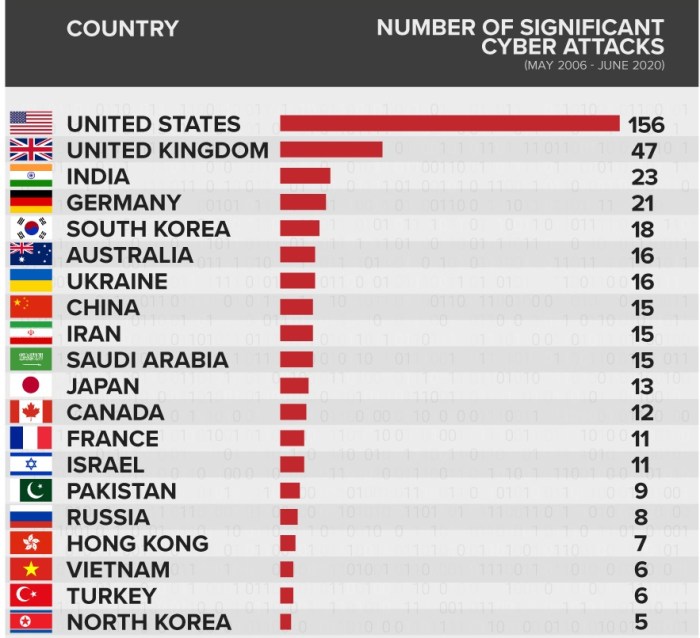
Europe has become the world’s most targeted region for cyberattacks, facing a growing threat landscape. This is due to a complex interplay of factors, including Europe’s economic and political prominence, its extensive digital infrastructure, and the presence of critical industries.
Expand your understanding about high performance car data informing battery performance with the sources we offer.
Economic and Political Factors
Europe’s economic and political significance makes it a highly attractive target for cybercriminals and state-sponsored actors. The European Union (EU) is the world’s largest single market, with a GDP of over €15 trillion. This makes it a lucrative target for cyberattacks aimed at disrupting businesses, stealing intellectual property, and extorting money.
- Economic Powerhouse:Europe’s strong economy, with a significant share of global trade and investment, makes it a prime target for cyberattacks aimed at financial gain.
- Political Influence:Europe’s political influence, particularly in international affairs, makes it a target for cyberattacks aimed at undermining its stability and influence.
- Critical Infrastructure:Europe’s reliance on critical infrastructure, such as energy, transportation, and telecommunications, makes it vulnerable to cyberattacks that could disrupt essential services and cause widespread economic damage.
Critical Infrastructure Sectors
Europe’s critical infrastructure sectors are highly vulnerable to cyberattacks. These sectors include energy, transportation, telecommunications, healthcare, and finance. These sectors are interconnected and rely on digital systems, making them susceptible to disruption or failure due to cyberattacks.
- Energy Sector:The energy sector is a critical target for cyberattacks, as it is essential for the functioning of modern economies. Attacks on energy infrastructure could disrupt power supplies, leading to widespread blackouts and economic disruption. Examples of such attacks include the 2015 Ukrainian power grid attack and the 2017 NotPetya ransomware attack, which affected businesses across Europe.
- Transportation Sector:The transportation sector is another critical target, as it relies heavily on digital systems for operations, including air traffic control, railway networks, and maritime shipping. Cyberattacks on transportation infrastructure could cause significant disruptions to travel and trade, impacting economies and public safety.
- Telecommunications Sector:The telecommunications sector is essential for communication, commerce, and public safety. Cyberattacks on telecommunications infrastructure could disrupt phone and internet services, leading to widespread communication outages and economic losses. An example of such an attack is the 2017 WannaCry ransomware attack, which affected telecommunications companies worldwide, including in Europe.
Types of Cyberattacks Targeting Europe: Europe Worlds Most Targeted Region For Cyberattacks
Europe is a prime target for cyberattacks due to its advanced digital infrastructure, high concentration of critical industries, and significant economic and political influence. The continent faces a wide range of cyber threats, each with its own motives and impact.
Types of Cyberattacks Prevalent in Europe
Cyberattacks targeting Europe can be categorized into several distinct types, each with its own characteristics and objectives. These include:
- Malware:This encompasses a broad range of malicious software designed to infiltrate systems, steal data, or disrupt operations. Examples include ransomware, which encrypts data and demands payment for its release, and spyware, which secretly monitors user activity and steals sensitive information.
- Phishing:This technique involves sending deceptive emails, messages, or websites that trick users into revealing sensitive information like login credentials, credit card details, or personal data.
- Denial-of-service (DoS) Attacks:These attacks aim to overwhelm a target’s servers or network with excessive traffic, rendering it inaccessible to legitimate users. This can disrupt business operations, cause financial losses, and damage reputation.
- Data Breaches:These involve unauthorized access to and theft of sensitive data from organizations’ systems. Data breaches can result in financial losses, reputational damage, legal liabilities, and compromised national security.
- Advanced Persistent Threats (APTs):These are sophisticated and persistent cyberattacks often conducted by nation-states or highly organized criminal groups. APTs involve long-term infiltration of target systems, data exfiltration, and espionage.
High-Profile Cyberattacks in Europe
Several high-profile cyberattacks have targeted Europe in recent years, highlighting the severity of the threat and the potential impact on critical infrastructure, businesses, and individuals.
- The NotPetya ransomware attack (2017):This global ransomware attack, believed to be orchestrated by Russia, significantly impacted businesses and organizations across Europe, including shipping giant Maersk and energy company Rosneft. The attack caused billions of dollars in damages and disrupted operations for weeks.
- The WannaCry ransomware attack (2017):This attack exploited a vulnerability in Microsoft Windows systems, affecting organizations and individuals worldwide, including the UK’s National Health Service (NHS). The attack crippled healthcare services, causing significant disruption and financial losses.
- The SolarWinds hack (2020):This sophisticated attack, attributed to Russia, involved the compromise of SolarWinds’ software update system, allowing attackers to infiltrate the networks of numerous organizations, including government agencies and private companies across Europe. The attack was significant for its scale, duration, and potential for espionage and data theft.
Evolving Nature of Cyberattacks in Europe
The cyber threat landscape in Europe is constantly evolving, with new threats emerging and existing ones becoming more sophisticated.
- Rise of ransomware-as-a-service (RaaS):This trend has made it easier for cybercriminals to launch ransomware attacks, even without technical expertise. RaaS platforms provide tools, infrastructure, and support for launching attacks, making them more accessible and dangerous.
- Increasing use of artificial intelligence (AI):AI is being used by both attackers and defenders in the cyber domain. Attackers are using AI to automate attacks, improve their effectiveness, and evade detection. Defenders are leveraging AI to improve threat detection, analysis, and response.
- Growing importance of critical infrastructure:Cyberattacks targeting critical infrastructure, such as power grids, transportation systems, and communication networks, pose a significant threat to national security and economic stability. These attacks can disrupt essential services, cause widespread damage, and potentially lead to social unrest.
Actors Behind Cyberattacks in Europe
The cyber threat landscape in Europe is complex and multifaceted, with a wide range of actors involved in launching attacks. Understanding the motivations and tactics of these actors is crucial for developing effective cybersecurity strategies. This section explores the key players behind cyberattacks targeting Europe, including state-sponsored groups, criminal organizations, and hacktivists.
State-Sponsored Actors
State-sponsored actors, often referred to as Advanced Persistent Threats (APTs), are government-backed groups that engage in cyber espionage, sabotage, and other malicious activities. These actors are typically highly skilled and well-resourced, and their operations are often politically motivated.
- Motives:State-sponsored actors are primarily driven by political and economic goals. Their motives include:
- Gaining intelligence on foreign governments, businesses, and individuals
- Disrupting critical infrastructure and economic activities
- Influencing public opinion and elections
- Protecting national interests and promoting their own geopolitical agenda
- Tactics:State-sponsored actors employ sophisticated tactics to achieve their objectives, including:
- Espionage:Gathering sensitive information through targeted hacking, phishing, and social engineering attacks
- Sabotage:Disrupting critical infrastructure, such as power grids, transportation systems, and communication networks
- Influence Operations:Spreading propaganda, misinformation, and disinformation to manipulate public opinion
- Cyber Warfare:Launching large-scale cyberattacks to cripple enemy systems and infrastructure
- Examples:Notable examples of state-sponsored actors targeting Europe include:
- Russia:Accused of conducting cyberattacks against Ukraine, the United States, and other Western countries, including the NotPetya ransomware attack in 2017
- China:Known for its advanced cyber espionage capabilities, targeting businesses and government agencies for intellectual property theft and economic advantage
- North Korea:Responsible for the WannaCry ransomware attack in 2017, which affected businesses and organizations worldwide, including those in Europe
- Iran:Suspected of launching cyberattacks against Israeli and Western targets, including the 2010 Stuxnet attack on Iranian nuclear facilities
Criminal Organizations
Criminal organizations are motivated by financial gain and often target individuals and businesses for profit. They employ various tactics, including ransomware, phishing, and malware attacks.
- Motives:Criminal organizations are primarily driven by financial gain, seeking to:
- Steal sensitive data, such as financial information, personal details, and intellectual property
- Extort money from victims through ransomware attacks
- Engage in fraud and identity theft
- Sell stolen data and access to other criminal actors
- Tactics:Criminal organizations utilize a wide range of tactics, including:
- Ransomware:Encrypting victims’ data and demanding payment for its decryption
- Phishing:Tricking victims into providing sensitive information through fake emails, websites, or social media messages
- Malware:Infecting victims’ computers with malicious software to steal data, control their systems, or launch further attacks
- Botnets:Networks of compromised computers used to launch distributed denial-of-service (DDoS) attacks, spam campaigns, and other malicious activities
- Examples:Prominent examples of criminal organizations targeting Europe include:
- The REvil ransomware gang:Responsible for the 2021 attack on JBS, a major meatpacking company, which disrupted supply chains worldwide
- The Trickbot botnet:A sophisticated botnet used for stealing financial information, spreading malware, and launching DDoS attacks
- The Conti ransomware gang:Known for targeting healthcare organizations and critical infrastructure, demanding high ransoms for data recovery
Hacktivists
Hacktivists are individuals or groups who use cyberattacks to promote political or social causes. They often target organizations or individuals they perceive as being responsible for injustices or wrongdoing.
- Motives:Hacktivists are motivated by ideological beliefs and seek to:
- Raise awareness about social or political issues
- Protest against government policies or corporate practices
- Disrupt the operations of their targets to cause damage or embarrassment
- Promote their own political or social agendas
- Tactics:Hacktivists employ various tactics, including:
- Website defacement:Altering the content of websites to display messages or propaganda
- DDoS attacks:Overloading websites with traffic to make them unavailable
- Data leaks:Exposing sensitive information to the public to embarrass or discredit their targets
- Social media campaigns:Using social media to spread their messages and mobilize support
- Examples:Notable examples of hacktivist groups targeting Europe include:
- Anonymous:A decentralized international group known for its high-profile attacks against governments, corporations, and other organizations
- LulzSec:A group of hacktivists known for their disruptive and humorous attacks, often targeting government and corporate websites
- The Syrian Electronic Army:A group suspected of being linked to the Syrian government, known for its attacks on media outlets and opposition websites
Impact of Cyberattacks on Europe
Cyberattacks on Europe have far-reaching consequences, affecting not only businesses and governments but also ordinary citizens. The impact of these attacks extends beyond immediate financial losses, encompassing economic, social, and political repercussions.
Economic Consequences
Cyberattacks can severely damage European economies. The cost of cybercrime is estimated to be billions of euros annually, impacting businesses, governments, and individuals.
- Financial Losses:Businesses suffer significant financial losses due to data breaches, ransomware attacks, and disruption of operations. For example, the NotPetya ransomware attack in 2017 caused billions of dollars in damages globally, affecting companies in Europe.
- Reduced Productivity:Cyberattacks can disrupt business operations, leading to downtime, lost productivity, and delayed projects. This impacts businesses’ profitability and competitiveness.
- Increased Insurance Costs:The rising threat of cyberattacks has led to increased insurance premiums for businesses, further adding to their financial burden.
Social Consequences
Cyberattacks can have significant social consequences, impacting individuals and communities.
- Identity Theft and Fraud:Data breaches can lead to identity theft and fraud, affecting individuals’ financial security and credit scores.
- Disruption of Services:Cyberattacks on critical infrastructure, such as healthcare systems, can disrupt essential services, impacting individuals’ access to healthcare and other vital services.
- Erosion of Trust:Cyberattacks can erode public trust in institutions and organizations, leading to increased anxiety and uncertainty.
Political Consequences
Cyberattacks can have significant political consequences, impacting international relations and national security.
- Destabilization of Governments:Cyberattacks on government systems can disrupt essential services, compromise sensitive information, and undermine the stability of governments.
- Escalation of Conflicts:Cyberattacks can be used as a tool of warfare, potentially escalating tensions between countries and leading to international conflicts.
- Weakening of Democracies:Cyberattacks can undermine democratic processes, such as elections, by spreading disinformation and manipulating public opinion.
Impact on Critical Infrastructure
Cyberattacks on critical infrastructure sectors, such as energy, transportation, and healthcare, can have devastating consequences.
- Power Outages:Cyberattacks on power grids can cause widespread power outages, disrupting essential services and impacting businesses and individuals. The Stuxnet worm, which targeted Iranian nuclear facilities in 2010, is an example of a cyberattack that disrupted critical infrastructure.
- Transportation Disruptions:Cyberattacks on transportation systems, such as air traffic control or railway networks, can lead to delays, cancellations, and safety risks.
- Healthcare System Disruptions:Cyberattacks on healthcare systems can disrupt patient care, compromise sensitive medical records, and put patients at risk.
Reputational Damage and Trust Erosion, Europe worlds most targeted region for cyberattacks
Cyberattacks can severely damage the reputation of businesses, governments, and individuals.
- Loss of Customer Trust:Data breaches and other cyberattacks can erode customer trust in businesses, leading to decreased sales and brand damage.
- Loss of Public Confidence:Cyberattacks on government systems can undermine public confidence in the government’s ability to protect citizens and national security.
- Increased Regulatory Scrutiny:Cyberattacks can lead to increased regulatory scrutiny and compliance requirements for businesses and organizations.
European Cyber Defense Strategies
Europe has recognized the growing threat posed by cyberattacks and has implemented a range of cybersecurity strategies and initiatives to strengthen its defenses. These measures aim to protect critical infrastructure, enhance national cybersecurity capabilities, and foster international cooperation.
Key Cybersecurity Strategies and Initiatives
European governments and organizations have implemented a number of key cybersecurity strategies and initiatives to address the increasing cyber threat. These include:
- The Network and Information Security (NIS) Directive:This directive, adopted in 2016, requires EU member states to implement national cybersecurity frameworks for critical infrastructure operators and digital service providers. It mandates risk assessments, incident reporting, and cooperation between national authorities.
- The Cybersecurity Strategy for the European Union:This strategy, adopted in 2017, Artikels the EU’s vision for a secure and resilient cyberspace. It focuses on enhancing cybersecurity capabilities, promoting research and innovation, and strengthening international cooperation.
- The EU Cybersecurity Act:This act, adopted in 2019, establishes a European Cybersecurity Agency (ENISA) to provide technical and operational support to EU member states. It also creates a framework for cybersecurity certification schemes for products and services.
- The European Cybercrime Centre (EC3):Established in 2013, EC3 is a unit within Europol that coordinates law enforcement efforts against cybercrime across Europe. It provides support to national authorities, facilitates information sharing, and conducts investigations into cybercrime.
Role of International Cooperation and Information Sharing
International cooperation and information sharing are crucial for effectively combating cyberattacks. The EU actively engages with international partners to address cyber threats, including:
- NATO:The North Atlantic Treaty Organization (NATO) plays a significant role in cyber defense. It provides a framework for cooperation between member states, conducts exercises, and develops cyber capabilities.
- The United Nations:The UN has established a framework for international cooperation on cybersecurity, including the UN Group of Governmental Experts on Developments in the Field of Information and Telecommunications in the Context of International Security.
- The Organization for Security and Cooperation in Europe (OSCE):The OSCE has a mandate to promote security and cooperation in Europe, including in the field of cybersecurity. It provides a platform for dialogue and cooperation on cyber issues.
Effectiveness of Current Cybersecurity Measures
While Europe has made significant progress in strengthening its cybersecurity posture, there are still areas for improvement.
- Gaps in Implementation:Some EU member states have been slower than others in implementing the NIS Directive and other cybersecurity measures. This has created inconsistencies in cybersecurity levels across the EU.
- Resource Constraints:Many countries face resource constraints in terms of funding, expertise, and infrastructure, limiting their ability to effectively combat cyber threats.
- Evolving Threat Landscape:The cyber threat landscape is constantly evolving, making it difficult to stay ahead of new and sophisticated attacks. This requires ongoing investment in research, development, and training.
Areas for Improvement
To enhance European cybersecurity, there is a need to:
- Improve Coordination and Collaboration:Strengthen coordination and collaboration between national authorities, private sector organizations, and international partners.
- Invest in Cybersecurity Capabilities:Increase investment in research, development, and training to build a more robust cybersecurity workforce and infrastructure.
- Promote Cybersecurity Awareness:Raise public awareness about cybersecurity threats and best practices to empower individuals and organizations to protect themselves.
- Strengthen International Cooperation:Enhance cooperation with international partners to address transnational cyber threats and share best practices.
Mitigating Cyber Risks in Europe
Europe’s vulnerability to cyberattacks necessitates proactive measures to mitigate risks. Individuals, businesses, and governments must work together to strengthen cybersecurity defenses and create a safer digital environment.
Best Practices for Cybersecurity Awareness, Incident Response, and Threat Intelligence
Cybersecurity awareness, incident response, and threat intelligence are crucial for effective risk mitigation. Here’s a table outlining best practices for each area:
| Area | Best Practices |
|---|---|
| Cybersecurity Awareness |
|
| Incident Response |
|
| Threat Intelligence |
|
The Importance of Cybersecurity Education and Training
Cybersecurity education and training are essential for building a resilient cyber ecosystem. Individuals, businesses, and governments all have a role to play:
- Individualsneed to be aware of common cyber threats and best practices for protecting their online identities and devices. This includes strong password management, avoiding suspicious links and attachments, and being cautious about sharing personal information online.
- Businessesmust invest in training programs for their employees to develop their cybersecurity skills and knowledge. This can include topics such as phishing awareness, secure coding practices, and incident response procedures.
- Governmentsshould promote cybersecurity education and training initiatives at all levels of society. This can involve funding research and development in cybersecurity, supporting educational programs, and establishing national cybersecurity awareness campaigns.