Privacy advocates slam uk anti encryption plans whatsapp – Privacy advocates are up in arms over the UK’s proposed legislation that would force messaging apps like WhatsApp to weaken their encryption. This move, which has been met with widespread criticism, has sparked a heated debate about the balance between national security and individual privacy in the digital age.
The UK government argues that these measures are necessary to combat terrorism and serious crime, claiming that encrypted communications provide a safe haven for criminals. However, privacy advocates contend that these plans would have a devastating impact on user privacy and security, potentially exposing personal data and communications to government surveillance.
UK Anti-Encryption Plans

The UK government is proposing legislation that would force messaging apps like WhatsApp to weaken their encryption, a move that has sparked widespread concerns about privacy and security. This proposal, which is still in its early stages, has drawn criticism from privacy advocates, tech companies, and security experts who argue that it could have significant negative consequences for individuals and society as a whole.
Rationale Behind the Plans
The UK government’s rationale for these plans is based on the argument that strong encryption makes it difficult for law enforcement agencies to access encrypted communications in criminal investigations. The government believes that this difficulty hinders their ability to combat terrorism, child exploitation, and other serious crimes.
The government’s stated objective is to ensure that law enforcement agencies have the necessary tools to investigate and prosecute criminal activity effectively.
Impact on User Privacy and Security
Weakening encryption in messaging apps would have a significant impact on user privacy and security. By forcing apps to create backdoors or vulnerabilities in their encryption, the government would essentially be creating a system where anyone with the right access could potentially intercept and read private communications.
This could have serious consequences for individuals, including:
- Increased risk of data breaches and theft: If encryption is weakened, it becomes easier for malicious actors to access sensitive data stored on devices and in messaging apps. This could lead to identity theft, financial fraud, and other forms of cybercrime.
- Compromised privacy and confidentiality: Weakening encryption would undermine the privacy and confidentiality of communications, making it possible for governments, corporations, or hackers to monitor conversations and access personal information.
- Reduced trust in digital communication: The public’s trust in digital communication would be eroded if they believe their messages are not truly secure. This could lead to a decrease in the use of messaging apps and other online services, hindering communication and collaboration.
- Potential for abuse: The ability to access encrypted communications could be abused by governments and other entities for political or personal gain. This could lead to censorship, surveillance, and the suppression of dissent.
Potential Risks to Personal Data and Communication
The potential risks to personal data and communication are significant. By weakening encryption, the government would be creating a system where personal data is more vulnerable to unauthorized access. This could have a wide range of negative consequences, including:
- Increased risk of surveillance: Weakening encryption would make it easier for governments and other entities to monitor communications, potentially leading to mass surveillance and a loss of privacy.
- Erosion of trust in online services: If users believe that their communications are not secure, they may be less likely to use online services, potentially hindering innovation and economic growth.
- Negative impact on human rights: The ability to access encrypted communications could be used to suppress dissent and target individuals based on their political beliefs or religious affiliations.
Privacy Advocates’ Concerns
Privacy advocates have expressed serious concerns about the UK’s proposed anti-encryption plans, arguing that they pose a significant threat to fundamental rights and freedoms. These concerns stem from the potential for increased government surveillance, erosion of online privacy, and the chilling effect on freedom of expression.
Government Surveillance and Erosion of Privacy
Privacy advocates fear that the UK’s anti-encryption plans will pave the way for widespread government surveillance, undermining the privacy of individuals and their online activities. They argue that forcing tech companies to weaken encryption would create vulnerabilities that could be exploited by governments to access sensitive personal data without proper judicial oversight.
This, they believe, would create a chilling effect on free speech and discourage individuals from expressing themselves freely online, fearing that their communications could be monitored by authorities.
Implications for Freedom of Expression
Privacy advocates argue that the UK’s anti-encryption plans could have a significant impact on freedom of expression. They believe that forcing individuals to use less secure communication channels would discourage them from expressing themselves freely, particularly on sensitive or controversial topics.
The fear is that individuals may be hesitant to engage in discussions or share information online if they believe that their communications are being monitored.
“Encryption is a fundamental right, not a privilege. It is essential for protecting privacy, freedom of expression, and the security of our digital lives.”
[Name of Privacy Advocate]
The Role of Encryption: Privacy Advocates Slam Uk Anti Encryption Plans Whatsapp
Encryption is a fundamental pillar of online privacy and security, playing a crucial role in safeguarding sensitive information and promoting trust in digital communications. Understanding the principles of encryption and its importance is essential in the face of growing threats to online privacy.
End-to-End Encryption Explained, Privacy advocates slam uk anti encryption plans whatsapp
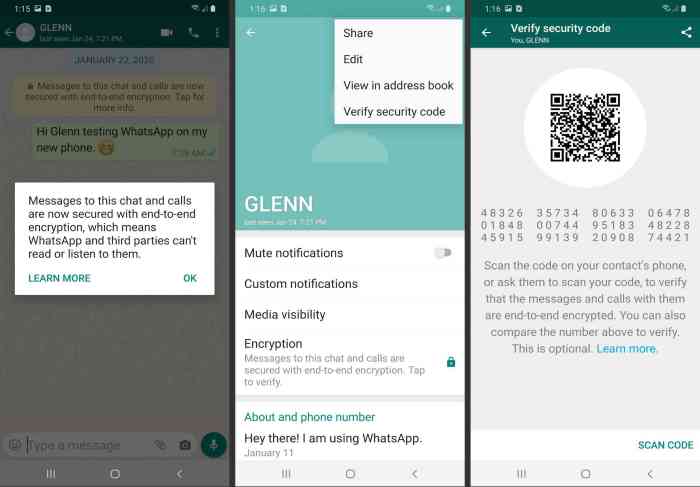
End-to-end encryption (E2EE) is a powerful security measure that ensures only the intended recipient can decrypt and read a message. This means that even if a message is intercepted, it remains unreadable to anyone other than the sender and receiver.
E2EE works by using unique keys for each user. When a message is sent, it is encrypted using the recipient’s public key. Only the recipient’s private key can decrypt the message.
Learn about more about the process of sustainable cooling for buildings huge opportunity for european startups in the field.
Benefits of Strong Encryption
Strong encryption offers numerous benefits for individuals and society as a whole.
Benefits for Individuals
- Protection of Sensitive Information:Encryption safeguards sensitive data like financial transactions, medical records, and personal communications from unauthorized access.
- Enhanced Privacy:E2EE protects users from surveillance and censorship, ensuring their online activities remain private.
- Secure Communication:Encryption allows individuals to communicate securely with others, regardless of location or network.
Benefits for Society
- Trust in Digital Communications:Strong encryption promotes trust in online platforms and services, encouraging greater adoption and use.
- Economic Growth:Encryption is essential for e-commerce, online banking, and other digital transactions, contributing to economic growth.
- National Security:Encryption protects critical infrastructure and sensitive government information from cyberattacks.
Consequences of Weakening Encryption
Weakening encryption would have serious consequences for online security and privacy.
- Increased Vulnerability to Cyberattacks:Weakening encryption would make it easier for malicious actors to access sensitive information, increasing the risk of data breaches and cyberattacks.
- Erosion of Trust in Digital Communications:Weakening encryption would undermine trust in online platforms and services, discouraging users from sharing sensitive information.
- Potential for Misuse by Governments:Weakening encryption could allow governments to access private communications without proper oversight, potentially leading to abuses of power.
Global Context and International Comparisons
The UK’s proposed anti-encryption legislation is not an isolated phenomenon. Governments worldwide are grappling with the challenges of balancing national security concerns with the protection of privacy and fundamental rights in the digital age. Examining similar measures in other countries and the broader global context provides valuable insights into the complexities of this issue.
International Comparisons
The UK’s proposal to force tech companies to provide access to encrypted communications mirrors similar efforts in other countries. For instance, the United States has long advocated for “lawful access” to encrypted data, arguing that it is necessary for law enforcement investigations.
Australia has implemented legislation requiring tech companies to provide “technical assistance” to authorities, including the ability to decrypt communications. However, these measures have faced criticism from privacy advocates and tech companies, who argue that they undermine security and privacy.
- Key Similarities:Many countries share the common goal of ensuring law enforcement’s ability to access encrypted data for investigations. This often involves requiring tech companies to provide technical assistance, including decryption capabilities, or backdoors.
- Key Differences:The specific mechanisms and scope of these measures vary significantly. For example, the UK’s proposal focuses on requiring companies to provide access to encrypted communications, while the Australian legislation is broader and includes access to data stored on devices.
Global Context and International Cooperation
The debate over encryption and law enforcement access is taking place within a broader global context of increasing cyber threats and the rise of transnational crime. Governments are facing growing pressure to address these challenges, which often involve encrypted communications.
However, the need for strong encryption to protect privacy and security is equally crucial. This tension presents significant challenges for international cooperation on cybersecurity.
- Challenges:Balancing national security interests with the protection of privacy and fundamental rights is a complex issue that requires international cooperation. Different countries may have varying legal frameworks and priorities, which can create obstacles to achieving consensus on encryption policies.
- Opportunities:International cooperation is essential for addressing the challenges of cybersecurity in the digital age. Sharing best practices, coordinating efforts, and establishing common standards for encryption can contribute to a more secure and resilient global cyberspace.
Potential Alternatives and Solutions
The UK government’s proposed anti-encryption measures have sparked a heated debate, raising concerns about the potential impact on privacy and security. While the government aims to address legitimate security concerns, the proposed approach risks undermining the very foundations of secure communication.
Fortunately, there are alternative solutions that can enhance security without compromising user privacy.
Alternative Approaches to Enhancing Security
The UK government’s desire to combat crime and terrorism is understandable. However, weakening encryption is not the answer. Instead, the focus should be on exploring alternative approaches that enhance security without compromising privacy. These approaches can be categorized into two main areas:
- Targeted Surveillance:Instead of weakening encryption for everyone, law enforcement should focus on targeted surveillance techniques. This involves obtaining warrants based on probable cause and using sophisticated tools to monitor specific individuals or groups suspected of criminal activity. This approach would ensure that the government’s surveillance powers are used responsibly and only when necessary.
- Collaboration and Information Sharing:Enhanced cooperation between law enforcement agencies, both domestically and internationally, can be crucial in tackling crime and terrorism. This includes sharing information and intelligence to identify potential threats and disrupt criminal activities.
- Investing in Technology:Instead of weakening encryption, the government should invest in technologies that can enhance security without compromising privacy. This includes research and development of tools that can detect malicious activity without decrypting communications.
Technological Solutions for Enhanced Security
Technology offers a range of solutions that can enhance security without compromising user privacy. Here are some examples:
- Zero-Trust Security:Zero-trust security models assume that no user or device can be trusted by default. This approach involves verifying every user and device before granting access to sensitive data.
- Homomorphic Encryption:This technology allows computations to be performed on encrypted data without decrypting it. This could enable law enforcement to analyze encrypted data without compromising privacy.
- Multi-Party Computation:This technique allows multiple parties to jointly compute a function on their private data without revealing their individual inputs. This could be used for secure data analysis and collaboration.
Balancing Security and Privacy in the Digital Age
The challenge of balancing security and privacy in the digital age is complex. However, a few key principles can guide policymakers:
- Proportionality:Surveillance measures should be proportionate to the threat they are designed to address. This means that the government should only use intrusive measures when less intrusive methods are not sufficient.
- Transparency and Accountability:Government surveillance programs should be transparent and accountable. This includes clear oversight mechanisms and independent audits to ensure that these programs are not abused.
- Privacy by Design:Technology should be designed with privacy in mind. This means incorporating privacy-enhancing features into systems and applications from the outset.